How I passed the OSCP
This is my story on how I passed the OSCP exam with 90 points in 10 hours
Background before exam
To begin with, I’m a student in my second year at INPT (National Institute of Posts and Telecommunications) in Morocco, I have no prior certification or work experience.
In summer of 2022 I had zero background of cybersecurity. I started by doing labs on HackTheBox and taking notes of each box I pwn. Ofcourse I followed write-ups when I was stuck but make sure to avoid them as much as you can. I learned so much from those labs to the extend that I became hooked into Red Teaming. I also participated in CTF competitions and gathered some humble knowledge and experience.
In summer of 2023 it was time to make the decision of buying the course (PEN-200) and starting the journey.
The journey begins!
I honestly enjoyed studying for the OSCP because I felt that I’m actually doing something useful, I also engaged with the community unlike school where I was wasting time studying just to pass a stupid exam. I did approximately 7 hours per day reading the course and doing the exercises, sometimes I studied for more than 10 hours staying up late cuz I’m a night owl :D . I finished the course material in nearly 2 months, then I moved to the labs. When I was stuck on a lab machine I asked for hints from members and staff in offsec’s discord server.
OSCP exam preparation
The exam is hard, I’m not saying this to disencourage you, but I have to pinpoint some facts.
There is 6 machines in the exam: 3 standalone machines (independent challenges) and 1 AD Set (3 machines in the Set). You need 70 points to pass, each standalone machine grants you 20 points (10 points for local.txt and 10 points for proof.txt).To get the proof.txt flag you need to do privilege escalation. For the AD set you need to pwn all machines including DC to get 40 points. So for example if you compromise the first and second machine of the AD set without the third (DC), you will get no points.
You can earn +10 bonus points from completing 80% course material and exercises of each module + rooting +30 Labs.
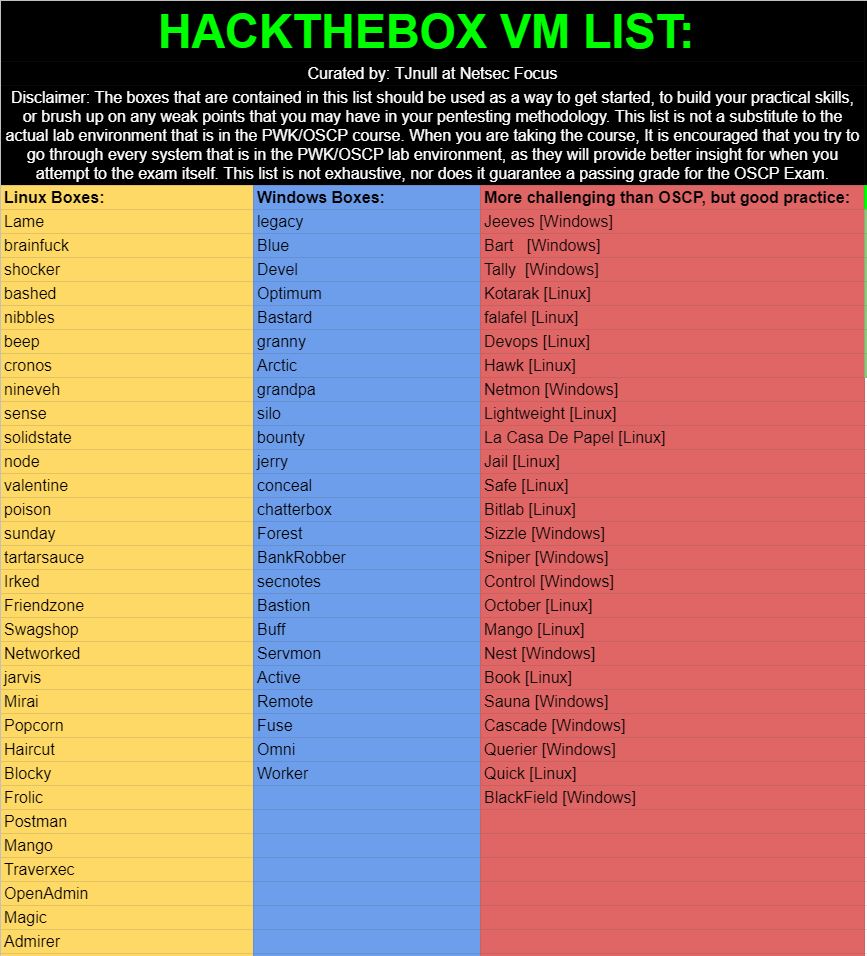
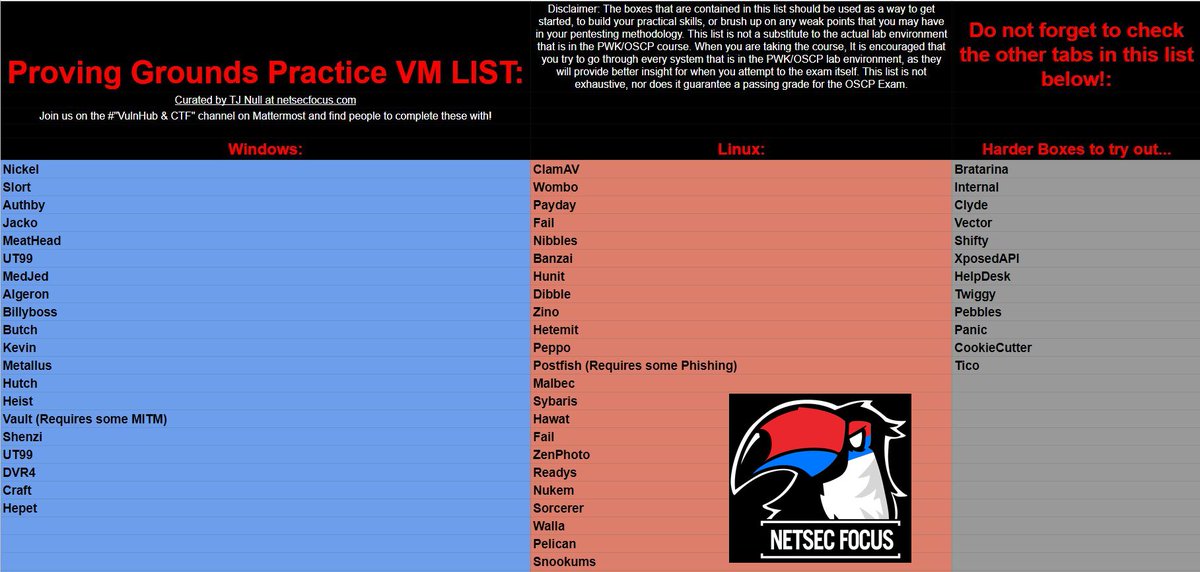
I started by doing HackTheBox TJ Null’s list boxes, Then OSCP’s LAB machines (OSCP A,B,C, MedTech, Relia) and finally Proving grounds TJ Null’s list. Every machine that I had finished was noted and saved in my documents for later use (in the exam day). I also did skylark from the offsec’s labs but that one remains optional because it contains technical skills beyond the scope of OSCP.
I honestly prefered LAB machines & proving grounds since it was much closer to the exam machines (real world scenarios) unlike HackTheBox which was kinda like CTFs.
Before the exam I had done +110 machines from HTB, PG and PEN-200 labs combined.
Exam’s day
I woke up at 6:45 AM(I actually couldn’t sleep well), I opened the proctored tool around 7:40 AM, went through the identification procedures and started my exam around 8:05 AM. I started by doing the Active Directory, I got initial access on the first machine but got stuck on the privilege escalation part. I took a break, got me a cup of coffee and started again, after few hours I got Administrator’s access. By 14:00 AM I had rooted the second machine and the domain controller.
Looking at nmap scans for possible credentials or attack vectors be like :
Next, I moved on to the standalone machines. I couldn’t find an attack vector on the first one so I immediately moved to the next. By 15:00 AM I had both local and proof flags. By now I knew I had enough points to pass but I had to check the last box. I eventually found an attack vector on the last machine and got local and proof flags by 17:33 AM.
Keep in mind that I have faced so many rabbit holes where bruteforcing takes so much time, passwords are impossible to crack and everything feels wrong. Yet I took too many breaks when I was stuck on initial foothold or privilege escalation, it helped me rethink what I’m doing and looking for a new attack vector back in the enumeration results.
Exam day be like:
After finishing the last machine and achieving 90 points I immidiately started writing the report.
Report writing
This is not your average school report, it’s serious you need to write a good and DETAILED report. Make sure to add every command and every screenshot that helped leading you to successfuly rooting the machine. If you use a new tool such as autorecon, ligolo-ng add from where and how you installed it, make sure to take a good screenshot of the local.txt and proof.txt flags.
For Windows :
For Linux :
The commands in your report will be replicated by a competent reader. So you have to write a report to the point that your grandma understands it. Keep in mind a bad report might lead to your failure.
Tips & Tricks
Enumerate,enumerate,enumerate. For better enumeration use Autorecon by Tib3rus.
Learn and use Ligolo-ng for pivoting.
Take a break the day before the exam.
Take breaks between machines and when you get stuck, trust me YOU WILL NEED IT.
Make your own cheat sheet of commands and “things to be aware of”.
Be aware of rabbit holes, if hydra takes more than 15 minutes to bruteforce then it’s not the intended path, if hashcat/JTR takes more than 10 minutes cracking a hash then it’s not meant to be cracked, if you follow a path for hours and couldn’t get access then go back to your scans and try another way.
Useful websites :
GTFObins : https://gtfobins.github.io/
Wadcoms : https://wadcoms.github.io/
Reverse shell generator : https://www.revshells.com/
Msfvenom payloads generator : https://infinitelogins.com/2020/01/25/msfvenom-reverse-shell-payload-cheatsheet/
Cheat sheet for OSCP (I recommend making and using your own) : https://github.com/0xsyr0/OSCP/
.gif)
.gif)
.gif)